Reduce risk by predicting threat actors
with Attack Simulation
How confident are you in your security of choice? How long can a threat persist in your network and devices undetected?
Shed light on your blindspots, misconfigurations and learn how your cybersecurity engines protect you – before the threat actors.
How does Attack Simulation work?
Select Test Package
Select or combine which test packages you want to measure up against. From Out of the Box Compliance tests validating aspects of DORA and NIST CSF 2.0, or put your vendor to the test.
Access Your Dashboard
Get access to your own dashboard, and gain insight into your security blindspots. Get actionable mitigations to further reduce your attack surface, curated for your environment.
Run Attack Simulations
Simulate a variation of cyberattacks to measure performance in detection and prevention. Simulate compliance violations and cyber threats. All tests map to the MITRE ATT&CK framework.
Jump to
Start here
Choose your test package
Select your test package, or discover more by contacting Rogue.
Log in to your Dashboard
You will receive an activation link in your inbox.
Run the Attack Simulation
Execute your selected test package by running it on your patient-0 computer.
Pay attention to your SIEM
Keep lookout for security logs and events generated during the attack cycle.
How well does it stop the attack?
See your preventive capabilities kick in and if it's able to stop it in its tracks.
Upload your results, discover security gaps
Read through how well you stopped certain types of attacks, and remediate your policies. Findings are mapped to the MITRE ATT&CK framework.
Re-run the Attack Simulation
Re-run the same Attacks to see how effective your remediations work.
Get The Rogue Report
A summary over uncovered risks with actionable recommendations. Uncover the value your current security provides, measuring return on protection. Highlighting misconfigurations, with benchmarks over advanced security capabilities. Mapped up with the controls you aspire to enforce.
Choose your simulation
Compliance Test Package
- DORA Assessment - Essential / Advanced
- NIST (CSF) 2.0 Protect - Advanced Assessment
Defensive Test Package
- Defensive Advanced Package - Endpoint Advanced - NGFW Filtering and Botnet Compromise.
- Defensive Essential Package - Endpoint Basic - NGFW Filtering and Botnet Compromise.
Cyber Hygiene Security Bundle
Advanced Compliance + Advanced Defensive Packages, includes The Rogue Report.
CATS - Continuous Automated Testing as a Service
All attack simulations including assessments from Defensive and Compliance packages and vendor assessments. Quarterly Rogue Report presentations, tailored to your business.
You can even automate it
Planning Phase
Set your security goals, identify your crown jewels - and define roles. Define the scope, assign responsibilites and identify scenarios.
Execute Attack Simulations
Quantify your security controls and protections. Simulate attacks and complinace violations in your environment. Elicit behaivoral-based EDR protections and black box technology.
Analyze Results
Uncover misconfigurations and security mishaps. Dvelve further into the data and gain actionable recommendations and mitigations tailored to your IT environment.
Remediate and Mitigate
Implement stronger policies, and configure your protections to protect against similar behaivor. Fix your misconfigurations, and evaluate vendors and their security products or services.
Validate Results
Re-run the same attacks to validate changed policies, and benchmark prevention capabalities. Compare the two states, and succsessfully validated your policies. If you still fall short, you might want to consider another solution.
Reflect & Automate
Automate the testing process, and contiously validate your security controls - track and detect security drift over time. Quarterly Rogue Reports and presentations.
Continously
Automated
Testing as a
Service
Automate testing using attack simulation to track to your cybersecurity performance. Detect security drift over time, and stress test POCs before investing in new products. Rogue CATS provides you with mitigations that integrates with what you use, to defend your business against the next attack campaign.
Tailored to your business

The Rogue Report
Benchmark your cybersecurity policies and engines.
Uncover how your current detection and prevention capabilities protects your business against threats.
The Rogue Report helps you validate deployed protection, providing actionable recommendations to further reduce your attack surface.
- 5Simulate behavioral-based attacks to elicit EDR reactions
- 5Benchmark your security tools against malicious threats
- 5Uncover how your NGFW reacts to malicious traffic
- 5Set higher expectations to your security vendors
- 5Understand your cybersecurity posture better
- 5Emulate the use of evasive malware
Inside the Rogue Report
Discover your attack surface
Shed light on potential blindspots and see how far an attacker can go by simulating real world threat tactics. Get a live view of patient-0 propagating in your network and see how your network design works in practice.
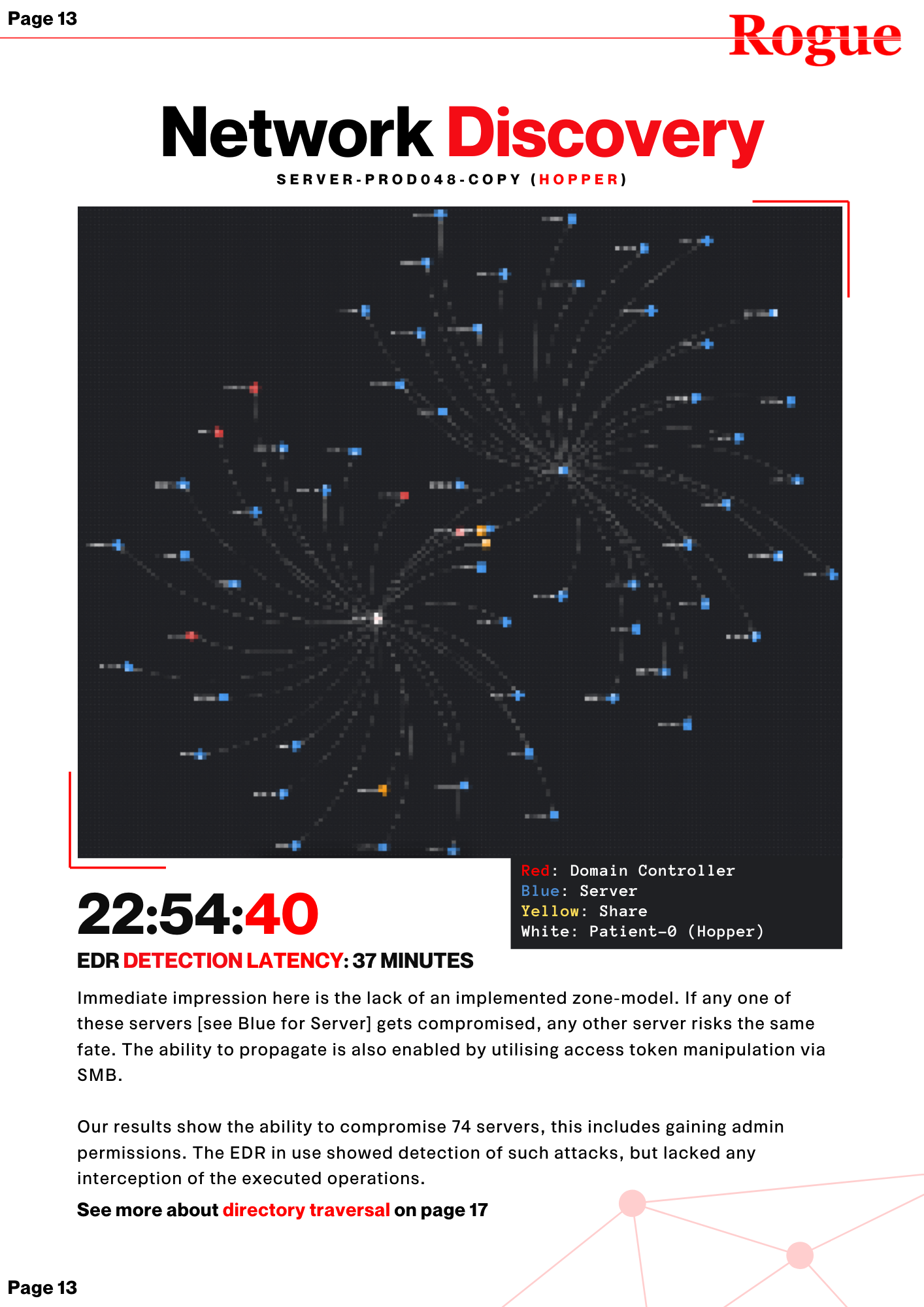
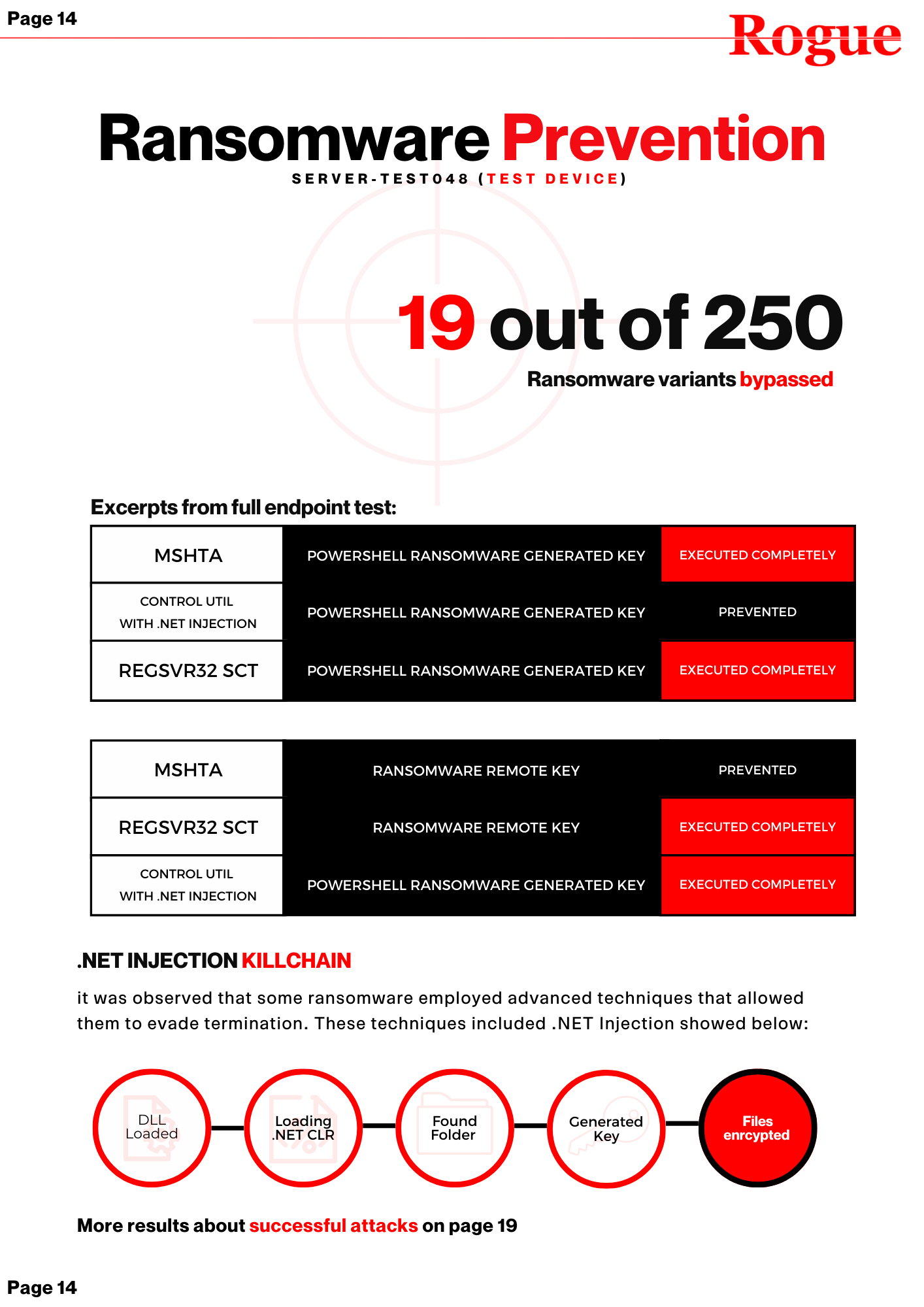
Test against ransomware
Cybersecurity vendors bet big on threat detection and prevention technologies, Rogue integrates the simulation with your endpoint product to pull out key findings such as: Threat prevention capabilites and accuracy.
Validate your security policies
Confident that your filters and policies are in place? Put it to the test by firing away malicious email and compare your catch rate results with other business with similar security tools.
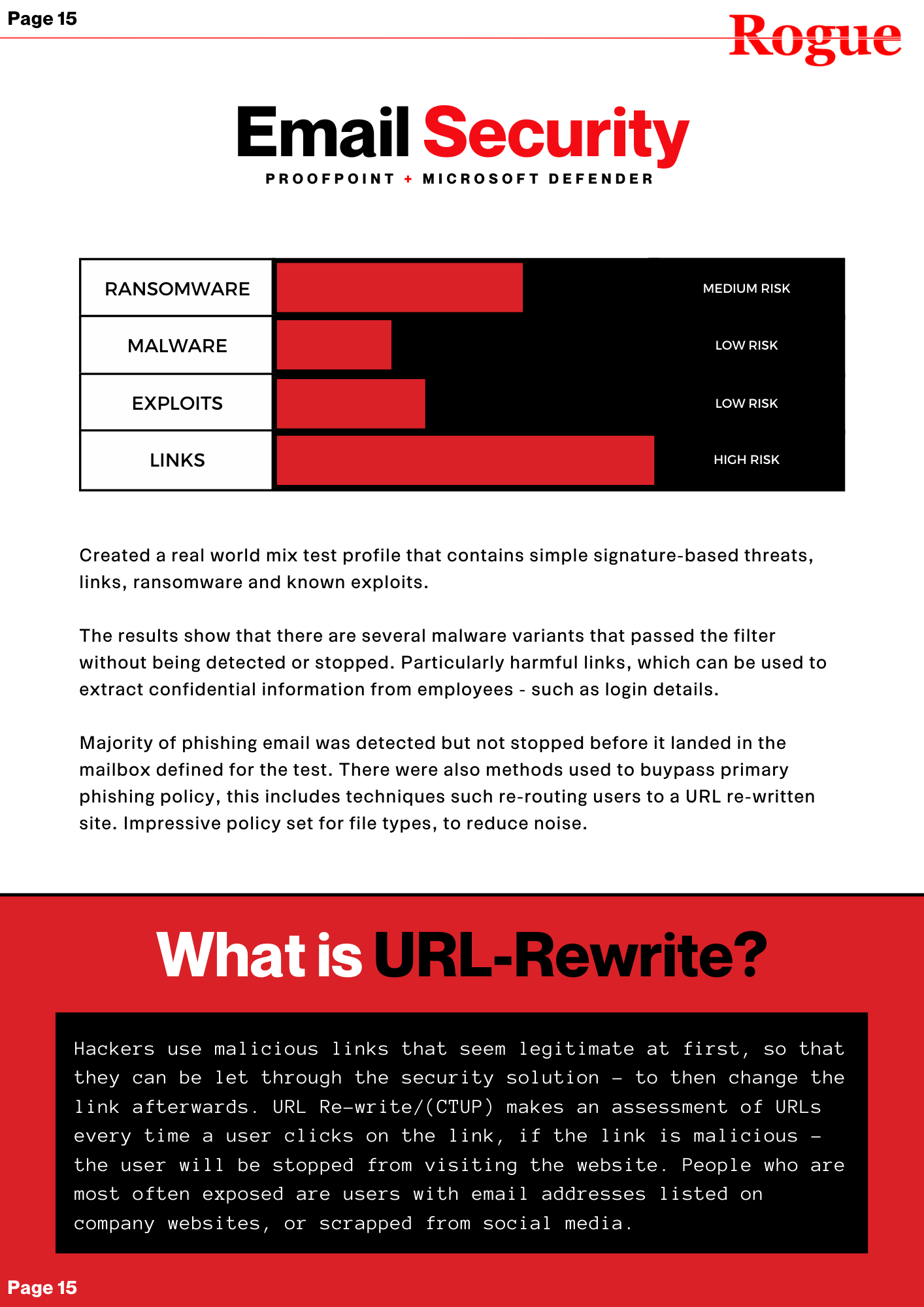
Calculate cybersecurity ROI
Rogue’s approach demystifies the impact of your cybersecurity tool stack. The goal is to illuminate the actualised return on protection, and the return on investment of your chosen security technology.
Measure cybersecurity effectiveness
How well does your defences stack up against the threat landscape? Get a risk score based on how you prevent and detect different threats on you network, endpoints, email and applications.
Get your Rogue Report
Measure your cybersecurity posture, test threat prevention capabilities – and discover vulnerabilities in your security architecture.

Frequently Asked Questions
How much does this cost?
Contact Rogue for more details around pricing.
Will this execute real malware?
Not exactly! There are tests that comprise of downloading known malware, but these are never executed. Some of the tests do include real TTPs leveraged by adversary groups, but again - no real malware will run.
Do I have to deploy and install agents?
No agent needed for any of the available assessments, CATS do give users the option to deploy up to 50 agents.
Should I ask my SOC before doing this?
Depends! We recommend businesses to collaborate and inform their SOC about any planned testing. If your SOC is managed by a security provider, read their policy about security testing - before running anything.
Can I get a regular pentest?
Sure! Rogue only offers penetration testing for web applications at this time, which provides you an assessment report - useful for audits. Ask for a quote here.
Single assessments or continously automated
Available Services
Attack Simulation Assessment
Point in time assessment that evaluates your cybersecurity technology, controls and policies against simulated cyberattacks safely. For measuring compliance or benchmarking the capabilites of your security arsenal.
CATS - Continously Automated Security Testing as a Service.
Run thousands of cyberattack and TTPs weekly. Tracking your security baseline over time, and detect security drift. See how much security your spending gives you, and qualify POCs before you pay.
Web Application Testing
Traditional pentest to find possible entry-points and opportunities. Uses tools to fuzz for API-endpoints on discovered variables, cookies and header key/values. Including a report with results and suggestions for mitigating vulnerabilities.