a part of Rogue Strategies
Insight Strategies
Make more informed decisions, turn data into a strategic asset.
Accurately quantifying cyber risks in financial terms is difficult. CISOs need to justify security investments and demonstrate how these align with and support broader business goals. While ensuring rapid adoption of new skillsets.
Many struggle with visibility and insight in cybersecurity due to the ever-changing threat landscape, the sheer volume of data, integration issues with security tools, budget constraints, regulatory complexities, rapid technological changes, and a shortage of skilled cybersecurity personnel. These challenges necessitate a continuous and dynamic approach, but also one that breaks silos and encourage cybersecurity culture across the organisation.
Shed light and uncover Shadow IT
Designed to identify and manage unauthorized IT systems and software within your organization. Rogue detects and analyze unsanctioned IT use, reducing risks and ensuring compliance. Rogue brings these hidden elements into the light, enabling you to enforce expected IT usage.
Navigating Cybersecurity Spending
In the face of economic uncertainties and tight budgets, CISOs often find themselves making tough choices based on costs. The key challenge is to balance financial constraints with the need for effective, all-around cybersecurity, moving from a reactive approach to a more proactive stance.
Address the use of Generative AI
AI applications like ChatGPT offer significant opportunities to enhance work efficiency, and so does new challenges, particularly in terms of data security. These advanced tools can inadvertently expose sensitive information to external threats. To counteract these risks, organizations must implement measures that protect the confidentiality, integrity, and overall security of their data.
Informed POCs and Acquisition
See through flashy sales presentations. Rather be guided through a more transparent and informed Proof of Concept (POC) process during security tool acquisitions. Rogue ensures that you make well-informed decisions when purchasing new cybersecurity solutions, considering both their promised effectiveness and integration capabilities within your existing setup.
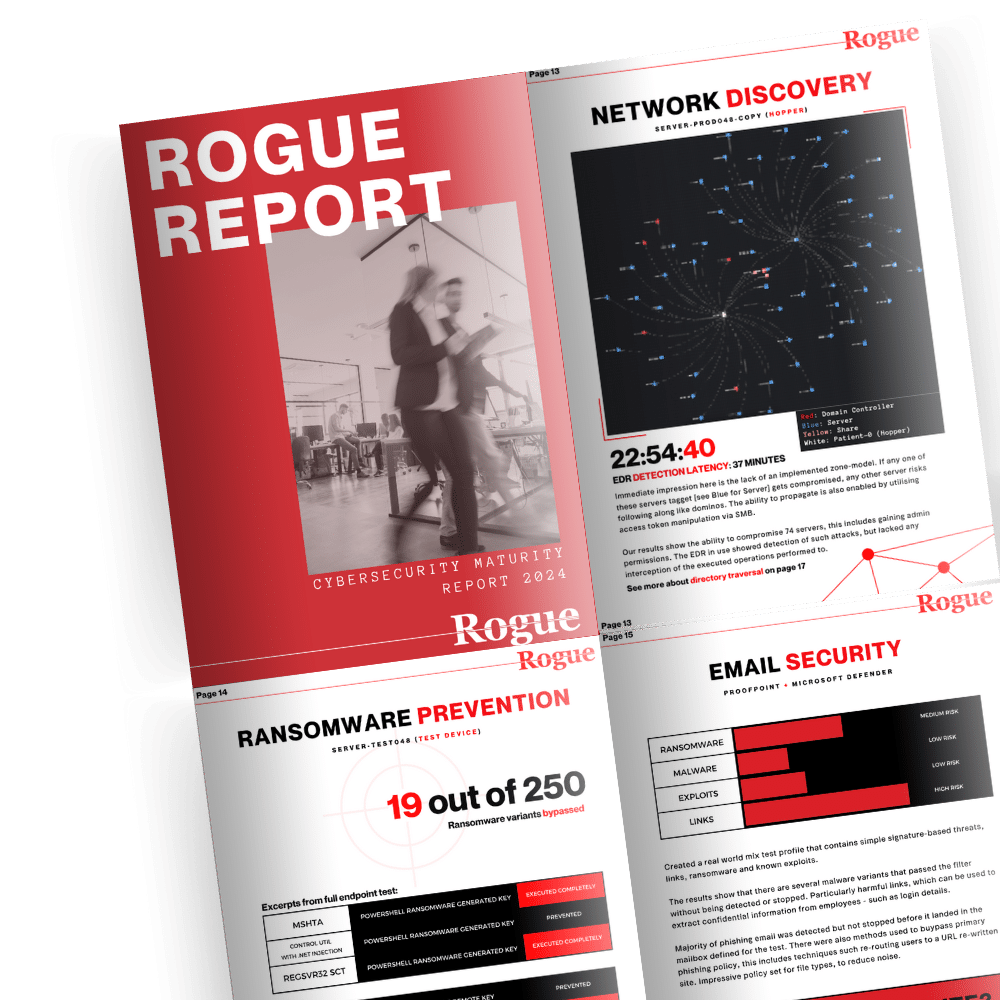
Get better insight with the Rogue Report
Get a clearer understanding of your current cybersecurity maturity-level, and map out low-hanging fruits that give more return on protection.